Tech
Ensuring Robust Digital Security: Best Practices for Businesses

Table of Contents
- Introduction to Digital Security
- Why Digital Security Matters
- Key Elements of Digital Protection
- Implementing Firewalls and Anti-Virus Software
- Secure Password Techniques
- Educating Employees on Cybersecurity
- Regular System Updates and Monitoring
- Incorporating Multi-Factor Authentication
- Conclusion: Maintaining Security Vigilance
Introduction to Digital Security
In today’s digital landscape, safeguarding sensitive information is paramount for any business committed to thriving in a tech-centric environment. The rapid advancement of technology means that businesses are prone to an ever-widening array of cybersecurity threats, each with its complexities and potential for harm. As discussed in Fortinet’s blog post on data breaches, maintaining an up-to-date cybersecurity framework is a critical business imperative for safeguarding assets. In an increasingly sophisticated era of data breaches, businesses must employ innovative means to prevent unauthorized access and system compromises.
Cybersecurity encompasses more than just protecting against hackers; it’s about fortifying all facets of business operations, from financial data to intellectual property. A holistic understanding of digital security necessitates addressing every potential vulnerability with nuanced solutions. Navigating this intricate landscape can be daunting, yet approaching it with strategic foresight offers businesses the chance to secure not just today’s assets but future growth and innovation.
Why Digital Security Matters
The increasing sophistication of cyber threats underscores the critical nature of digital security. In an age where attacks are more frequent and intricate, businesses of all sizes find themselves in the crosshairs of cybercriminals. The financial toll of cyberattacks can be staggering, with incidents costing businesses millions—or even billions—of dollars annually. Beyond stark monetary losses, cybersecurity breaches can severely damage a brand’s reputation, weaken consumer trust, and impose onerous legal liabilities.
Data underscores this urgency. Studies reveal that a single data breach can lead to astronomical costs comprising direct response expenses and indirect losses associated with customer mistrust and reputation damage. Therefore, implementing effective cybersecurity measures is not merely about safeguarding data—it’s essential to maintaining business continuity and resilience.
Key Elements of Digital Protection
Creating an effective digital security strategy involves a multi-layered approach that integrates several vital components, each contributing to a fortified defense system. These components range from technical defenses like firewalls and encryption to human-centric initiatives such as employee training and awareness programs. Together, they create a robust defense mechanism to counteract various cyber threats.
By considering each element’s unique contributions, businesses can craft a tailored protection plan that meets their needs. Detailed consideration of a comprehensive security strategy is essential for establishing a balanced, effective, and adaptable digital security policy capable of responding to dynamic threats.
Implementing Firewalls and Anti-Virus Software
Firewalls are essential components in the armor of digital security, serving the critical function of filtering network traffic to block unauthorized access based on predetermined security rules. These protective barriers are instrumental in preventing unwanted intrusions that can compromise the integrity of a business’s network. The deployment of robust anti-virus software complements firewalls, offering a secondary layer of defense that identifies, quarantines, and eradicates malicious entities before they cause significant harm.
For businesses, the challenge lies in selecting tools that suitably balance cost, performance, and security benefits. While large corporations might invest in sophisticated enterprise-level solutions, SMEs (small and medium enterprises) often find solace in budget-friendly alternatives that effectively cater to their specific threat landscapes.
Secure Password Techniques
In cybersecurity, passwords often serve as the gatekeepers of digital identity. Unfortunately, weak or reused passwords remain a primary vulnerability exploited by attackers. Strengthening this line of defense through secure password techniques is of the utmost importance. This means utilizing long, complex combinations of characters and regularly updating password credentials to prevent unauthorized access.
Password management tools facilitate this practice, providing a secure repository for managing numerous complex passwords without sacrificing usability. By empowering users with easily accessible and secure password storage, businesses can bolster their overall security posture without complicating daily operations.
Educating Employees on Cybersecurity
While technology is indispensable in digital security, human awareness and preparedness are equally crucial. Employees frequently become the first line of defense against tactics like phishing and social engineering. Regular security awareness training is essential in empowering employees with the knowledge and skills to effectively identify and respond to threats.
Establishing a security awareness culture can substantially mitigate human error risks. Businesses transform their workforce into vigilant protectors of sensitive information by prioritizing comprehensive training that recognizes malicious emails, implements secure data handling practices, and understands communication protocols.
Regular System Updates and Monitoring
Maintaining timely system updates and monitoring activities is a cornerstone of comprehensive cybersecurity. Software vendors regularly release updates and patches that address security vulnerabilities, and ensuring these updates are promptly applied is a fundamental duty for businesses looking to guard against cybercriminals’ exploitation.
Complementing updates with robust monitoring capabilities enables businesses to maintain real-time insight into system functionalities. Companies can react swiftly to mitigate damage, thwart potential breaches, and maintain data integrity by continuously watching for anomalies and possible threats.
Incorporating Multi-Factor Authentication
Multi-factor authentication (MFA) significantly strengthens access protocols by requiring additional layers of verification beyond simple passwords. This authentication process fortifies systems by making unauthorized account access considerably more challenging, even in the event of password compromise.
Integrating MFA is usually straightforward, involving the addition of verification steps such as SMS codes or authentication apps. The added security MFA provides significantly outweighs the minor disruptions it may introduce, making it an essential component of a robust digital security strategy.
Conclusion: Maintaining Security Vigilance
Maintaining effective defensive measures requires ongoing vigilance and evolution in an era of continually evolving digital threats. Businesses must regularly evaluate and enhance security protocols to remain defensive against emerging threats. By prioritizing cybersecurity, organizations safeguard their tangible and intangible assets and cultivate a foundation of customer trust and reliability.
Ultimately, embracing digital security is more than a protective measure—it represents an unwavering commitment to ensuring sustainable growth within an increasingly complex digital landscape. Staying informed and proactive is the strongest bulwark against the myriad challenges businesses confront in today’s digital realm.
Tech
The Role of Sensors and Controllers in Laboratory Incubator Performance
Laboratory incubators serve as the backbone of modern scientific research, supporting the cultivation of cell cultures, microbiological analyses, and numerous experimental protocols that require precise environmental control. Their accuracy and reliability are heavily dependent on the synergy between advanced sensors and nuanced control systems that maintain ideal conditions for scientific work. When these sophisticated machines require expertise, it’s essential to rely on industry professionals, such as those specializing in laboratory incubator repair Delaware, to ensure consistent and dependable performance.
Even minor variations in temperature, humidity, or gas levels within an incubator can compromise the integrity of research. This level of precision, and the mechanisms that ensure it, have been elevated immensely with modern diagnostic sensors and smart automation, setting new standards for reproducibility in laboratory studies. The capability to monitor data remotely and maintain tight tolerances is transforming how laboratories uphold experimental validity, minimize contamination risk, and comply with regulations for sensitive research environments.
Importance of Precise Environmental Control
Laboratory incubators are designed to provide controlled conditions crucial to biological and chemical experiments. Stable temperature, humidity, and gas concentration are fundamental for cellular growth, tissue development, and chemical reactions. Even subtle shifts can introduce variability, impair reproducibility, and threaten the success of high-stakes research such as vaccine development or genetic engineering.
The ripple effect of environmental instability within incubators means risk for cross-experiment contamination and erroneous data—risks that healthcare, pharmaceutical, and clinical research labs cannot afford to take. With ever-tighter regulatory requirements, precise control and reliable monitoring become prerequisites for both research integrity and compliance.
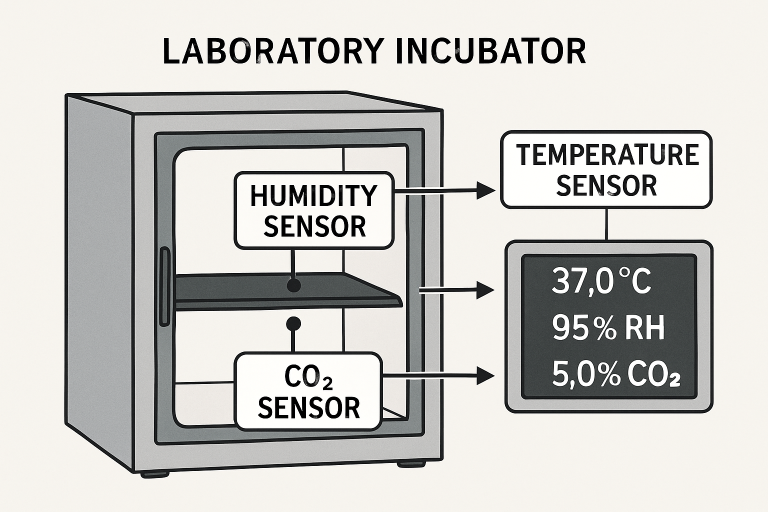
Key Sensors in Laboratory Incubators
Modern incubators rely on an array of robust sensors to continually monitor and regulate key parameters:
- Temperature Sensors: Platinum resistance devices, such as PT100s, are widely adopted for their stability and accuracy, which are essential for protocols that demand exact thermal profiles. These sensors are carefully positioned within the incubator to capture both localized and overall variations in temperature.
- Humidity Sensors: By quantifying relative humidity, these sensors prevent conditions that could lead to sample desiccation or mold growth, which are frequent causes of experiment failure in tissue culture.
- CO₂ Sensors: Accurate carbon dioxide measurement sustains the delicate pH of media in cell culture applications. Advanced photoacoustic and infrared sensors offer reliable CO₂ quantification, accommodating a wide range of research needs.
Advanced Control Systems
The intelligence of an incubator lies within its control systems, which synthesize constant sensor input to adjust environmental outputs in real-time:
- Automated Feedback Mechanisms: Feedback loops operate heaters, chillers, and gas valves with split-second responsiveness, maintaining setpoints with minimal variance. This minimizes manual intervention and human error, thereby strengthening overall experiment reliability.
- PID Controllers: Proportional-Integral-Derivative (PID) controllers calculate and correct deviations between actual and desired states. This leads to rapid error correction and remarkable environmental stability—critical for sensitive experimental timelines.
Integration of Smart Technologies
The digital transformation of laboratory equipment is changing how scientists interact with their incubators and data:
- Remote Monitoring: Cloud-based interfaces and mobile apps empower researchers to view live parameter data and receive deviation alerts from anywhere, drastically reducing response times and safeguarding research assets. This is invaluable for labs operating under strict quality controls or managing long-duration studies.
- Data Logging and Analytics: Incubators now offer continuous data recording, building a detailed environmental history that supports troubleshooting and advanced data analysis. Laboratories use these insights to optimize protocols and achieve higher reproducibility rates, which are increasingly required for publication in major journals.
Challenges and Solutions
Even with technological advances, practical challenges persist in maximizing incubator performance:
- Sensor Calibration: Sensor drift, caused by environmental exposure or prolonged use, can result in misleading data. Scheduled calibration and proactive maintenance protocols are necessary measures for ensuring ongoing accuracy—especially in labs where regulatory audits are a constant consideration.
- Contamination Risks: The enclosed, moisture-rich environments ideal for cultures are also attractive to contaminants. Solutions such as integrated HEPA filters, antimicrobial coatings, and automated UV sterilization cycles dramatically reduce the incidence of cross-contamination and lost samples.
Future Trends in Incubator Technology
As technology continues to evolve, key trends are emerging in laboratory incubator design:
- Enhanced Automation: Artificial intelligence is being developed to anticipate and respond to environmental changes proactively, thereby reducing human oversight and enabling real-time optimization for even the most sensitive experiments.
- Energy Efficiency: Sustainability is an increasing priority. Newer incubators are leveraging design innovations and material science advancements to reduce energy consumption without compromising performance, helping labs lower their operational costs and environmental impact.
- Improved User Interfaces: More intuitive touchscreens and app-based controls are making incubator operation easier and more accessible, shortening the learning curve for new users and minimizing errors.
Conclusion
Reliable laboratory incubator performance is the result of a sophisticated marriage between advanced sensors and responsive control systems. These innovations empower researchers to maintain exact conditions and focus on groundbreaking discoveries. As digital technologies, automation, and sustainability practices move to the forefront, the future of laboratory incubators promises even greater accuracy, efficiency, and scientific impact.
READ ALSO: Advancements in Battery Testing: Enhancing Safety and Reliability
Tech
Choosing the Right Casters for Your Application
Introduction
Enhancing mobility in equipment—whether industrial machinery, medical devices, or office furniture—relies on selecting the right casters for your specific needs. The process isn’t about picking wheels but finding the ideal match to ensure optimal performance, durability, and safety. Whether you’re retrofitting existing equipment or customizing new projects, understanding how to select wheels for carts is foundational to designing effective solutions for your workplace or facility.
Applications differ widely, and so does the choice of casters. Selecting the correct type and material not only guards against unnecessary wear and tear but can enhance operational efficiency and reduce maintenance costs in the long term. Understanding caster fundamentals also helps prevent floor damage and fosters a safer working environment.
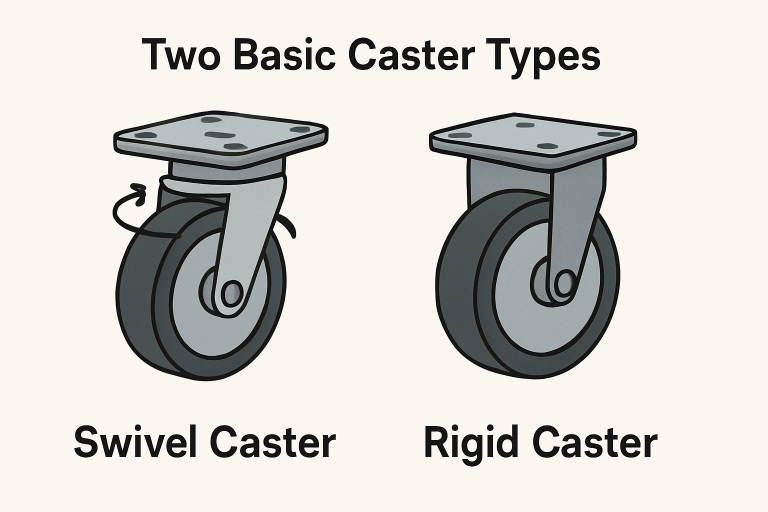
Understanding Caster Types
Casters are designed in two primary categories: swivel and rigid. Recognizing how they function and where they excel sets the stage for further customization.
- Swivel Casters: These offer 360-degree rotation, making them an essential choice for applications where frequent directional changes are necessary, like in hospital beds, rolling tool chests, or restaurant carts, where nimble navigation is critical.
- Rigid Casters: Built to move in only one direction, rigid casters are best for applications that need straight-line stability, such as conveyor equipment or heavy-duty racks that are seldom repositioned.
For many projects, combining both types—swivel on one end, rigid on the other—delivers a blend of maneuverability and stability, accommodating a wide range of operational needs.
Key Factors in Caster Selection
Selecting casters isn’t only about mobility. Some critical elements require careful assessment:
- Load Capacity: Underestimating the weight your equipment needs to support can lead to caster failure, equipment damage, or safety hazards. Always match or exceed the weight guidelines provided by the caster manufacturer.
- Flooring Type: Match the wheel’s composition to your flooring to minimize surface damage. For example, soft wheels are ideal for hardwood, while harder wheels fare better on carpet or concrete.
- Environmental Conditions: Exposure to water, chemical agents, or high heat may necessitate special materials. Neglecting this consideration can lead to corrosion or accelerated wear.
Carefully weighing these factors before purchase ensures that the selected caster will be functional and safe in its environment. For a deeper dive into how workplace equipment can impact safety and productivity, visit this comprehensive overview by Industrial Magazine.
Material Considerations
Material choice influences everything from load rating to the type of maintenance required. Here are the most common options:
- Polyurethane Wheels: Polyurethane is often considered the go-to for multipurpose use. It combines resilience with floor protection, and its resistance to abrasion and chemicals makes it valuable in warehouses and healthcare settings.
- Rubber Wheels: Noted for their quiet, cushioned ride, rubber wheels shine in office environments or on delicate floors but may degrade faster under constant heavy loads.
- Metal Wheels: The ultimate workhorse, metal wheels can bear extreme weights and withstand rough usage. However, they are noisier and can damage floors without proper preparation.
Considering the likely environment in terms of traffic, noise tolerance, and floor quality will help you choose the optimal material for your casters.
Load Capacity and Durability
Load capacity isn’t just the sum of what a single caster can handle; divide the equipment weight (including its contents) across the number of casters, then add a safety factor to allow for uneven weight distribution and shock loads. Overloading casters results in deformation, braking failure, and can present an immediate hazard in busy environments.
Manufacturers provide clear load ratings. Ignoring these guidelines is a primary cause of premature caster failure. Ensure every component is up to the task, especially if mobility is vital for your application’s productivity or safety.
Environmental Factors
The operational setting significantly impacts caster longevity and function. Consider these environmental elements:
- Temperature Extremes: Plastic and rubber compounds may become brittle and lose performance at very low temperatures, while high heat can degrade specific polymers and lubricants.
- Exposure to Chemicals: Industrial cleaning agents, oils, and solvents can rapidly degrade unsuitable wheel materials, leading to splitting or losing traction.
- Moisture Levels: High humidity or frequent water exposure demands corrosion-resistant designs—stainless steel or specialized coatings are preferable in these scenarios.
Factoring in the daily environment ensures longevity and optimal ROI from your caster investment. Machine Design also provides guidance on selecting industrial hardware for challenging environments.
Maintenance and Safety
Routine inspection and maintenance are non-negotiable for any equipment with casters. Schedule regular checks according to the manufacturer’s recommendations. Focus on:
- Checking wheels and axles for wear or cracks.
- Removing any debris or buildup from wheel treads.
- Lubricating bearings and swivels to maintain silent, smooth operation.
Sticking to a proactive maintenance routine extends service life and helps mitigate workplace accidents caused by faulty mobility equipment.
Conclusion
Choosing the correct casters means looking beyond basic functionality to evaluate load capacity, material construction, and the operational environment. Given the array of available options, an informed selection empowers your equipment to deliver optimal utility, protecting your floors, staff, and investment. For more guidance or to shop for quality solutions, explore wheels for carts designed for various commercial and industrial needs.
Tech
Heavy-Duty Mobility Solutions for Industrial Efficiency

Industrial operations rely heavily on equipment and machinery that can withstand demanding conditions while maintaining smooth and efficient workflows. One often overlooked factor in achieving operational efficiency is mobility—how equipment moves, adapts, and absorbs the stresses of daily use. Heavy-duty mobility solutions are designed to support substantial loads while minimizing disruptions caused by uneven surfaces, vibrations, and repetitive motion. Incorporating small shock absorbing casters into industrial carts, platforms, and transport systems can significantly enhance stability and reduce wear and tear, creating a safer and more reliable work environment.
These solutions are particularly valuable in facilities where frequent relocation of machinery or materials is required. By combining robust construction with features like shock absorption, industrial mobility systems help maintain productivity, reduce downtime, and extend the lifespan of equipment. Thoughtful mobility design ensures that operational flow remains uninterrupted, supporting overall efficiency and creating a more ergonomic workspace for employees handling heavy loads.
Advancements in Caster Technology
Recent years have seen a significant leap forward in caster engineering, specifically tailored to meet the needs of heavy-duty applications. Notably, extra-heavy-duty dual-wheel casters are now revolutionizing how plants move their heaviest and most valuable assets. Built for exceptional load capacities, these casters can withstand rigorous industrial use without succumbing to deformation or performance fatigue. Their dual-wheel design distributes weight more effectively, reducing stress on floors and enhancing both maneuverability and long-term durability.
Shock-absorbing mechanisms within modern casters not only protect delicate loads but also contribute to reduced noise and smoother transport. These improvements have enabled facilities to expand their capabilities, allowing them to confidently move precision equipment across varied terrains and tight spaces.
Automated Carousel Systems
Material handling is undergoing a digital revolution, with automated carousel systems at its heart. These systems use vertical or horizontal carousels to optimize space, sort inventory quickly, and automate the movement of parts and equipment. Automating these workflows not only reduces labor costs but also minimizes picking errors and eliminates unnecessary storage space, thereby freeing up valuable floor space for other activities.
Facilities without automation often grapple with workflow interruptions due to manual searching, misplaced goods, or inefficient storage. In contrast, automated carousel systems bring materials directly to workers, improving picking precision while drastically reducing walk time and fatigue.
Digital Transformation in Heavy Equipment
The mobility of heavy equipment is now being redefined not just by mechanical solutions, but also by digital innovation. Connected sensors and software-driven diagnostics empower real-time equipment and asset tracking, allowing teams to anticipate maintenance needs and prevent costly, unexpected breakdowns.
The Role of Digital Twins
One of the most impactful advancements is the adoption of digital twins—data-driven virtual representations of physical machinery. These models are used to simulate, test, and continuously improve processes without interrupting production lines physically. By proactively identifying performance bottlenecks or potential failures, companies can react swiftly and optimize their layouts and workflows to improve efficiency. As businesses leverage these technologies, they not only gain visibility but also actionable insights for continual improvement and cost reduction.
Sustainable Mobility Solutions
With sustainability goals rising to the forefront, eco-friendly mobility solutions are quickly becoming the industry standard. Electrified tuggers, battery-powered loaders, and hydrogen-powered vehicles offer high torque for moving large loads, while also producing far lower carbon emissions compared to their diesel or gasoline-powered predecessors. These systems benefit both the environment and plant economics by reducing fuel and maintenance costs while ensuring compliance with tightening regulatory requirements.
In sustainable operations, the use of recyclable or renewable materials in caster manufacturing, as well as the adoption of low-resistance wheels, is also gaining ground, providing another layer of efficiency by minimizing energy consumption. Beyond the direct savings, sustainable initiatives also help companies attract investment and meet the increasing expectations of eco-conscious stakeholders.
Challenges and Considerations
Transitioning to next-generation mobility systems presents challenges. Initial capital investment can be significant, and staff may require specialized training to adapt to new equipment or automation platforms. Integrating new technologies into legacy systems sometimes necessitates temporary disruptions or phased implementations. Organizations should conduct thorough assessments, pilot projects, and vendor consultations to understand both the short-term impacts and the long-term efficiency gains of such upgrades.
Conclusion
As industrial operations become increasingly complex and competitive, the importance of robust, adaptable mobility solutions cannot be overstated. With advancements in caster technology, the adoption of automated systems, the rise of digital tools, and an urgent shift toward sustainability, manufacturers can achieve safer, smarter, and more sustainable operations. Investing in these innovations not only reduces downtime and operational risk but also positions organizations at the forefront of industrial efficiency and resilience for years to come.
-

 Home Improvement1 year ago
Home Improvement1 year agoEasy Ways to Clean and Maintain Your Foam Play Mat
-

 Celebrity1 year ago
Celebrity1 year agoWho Is Andrew Santino Wife? The Full Story
-

 Tech1 year ago
Tech1 year agoExplore iZoneMedia360 .Com Features & Benefits
-

 Entertainment1 year ago
Entertainment1 year agoRemembering Melanie Olmstead Yellowstone’s Unsung Hero
-

 Uncategorized1 year ago
Uncategorized1 year agoPrairie Dog Guide: Habitat, Behavior, and Conservation
-

 Celebrity1 year ago
Celebrity1 year agoA Deep Dive into Jeremy Allen White Movies and TV Shows
-

 Apps & Games1 year ago
Apps & Games1 year agoThe Pizza Edition Games: A Perfect Slice of Fun and Flavor
-

 Business1 year ago
Business1 year agoHow Influencersginewuld Shapes the Future of Branding





